Applying Email Security Policies
How can I apply Email Security Policies?
There are six MailWall policies:
- Web Bugs
Malicious pieces of code hidden in email messages which allow the sender to track the opening and reading of the email. Commonly used in Spam messages and poorly written newsletters.
- Suspect HTML
HTML code in email messages which could pose a moderate risk to privacy. Examples include multiple unbalanced tags and too many off-site links. This policy will block some legitimate newsletters and some automatically (computer) generated email notifications.
- Dangerous HTML
HTML code in email messages which could pose a major security risk. Examples include IFrame, Form, Script and Object Codebase tags.
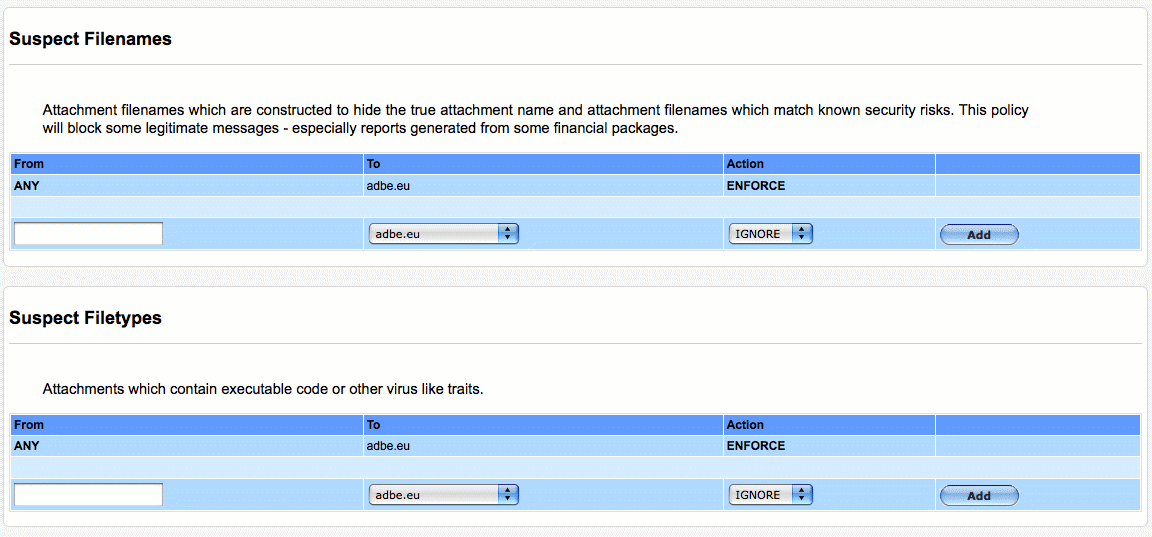
- Suspect File names
Attachment file names which are constructed to hide the true attachment name and attachment file names which match known security risks. This policy will block some legitimate messages - especially reports generated from some financial packages.
- Suspect File types
Attachments which contain executable code or other virus like traits but are not identified as a known virus.
- Suspect Content
Messages designed to avoid being scanned. Examples include Unreadable messages, Password-Protected Archives, Partial Messages and External Message Bodies.
Managing email policies is performed in a similar logical manner to adding rules on commercial firewall appliances.
Policies are either Enforced or Ignored on a per sender, per recipient basis. Each policy has a default “catch all” rule and multiple enforcing or ignoring rules.
By default, all default policies rules are set to be Enforced on a domain wide basis meaning that in the absence of any other rules to the contrary, the policy will be enforced for all email going to that domain.